Free Software Risk Assessment Tool
AI Cyber Risk Assessment
Software Name
November 11, 2025
Table of Contents
- Executive Summary
- Overall Risk Score & Recommendations
- AI Risk Scorecard
- Comparative Security Benchmarking
- Historical Trends & Future Risk Projections
- Data Protection & Residency Evaluation Matrix
- VirusTotal Domain Report
Understanding Your AI-Powered Report
Welcome to your AI-powered Cyber Risk Assessment report guide. This detailed webpage will help you interpret each section of your personalized risk analysis, based on your use of open-source or commercial software. Designed with small to medium-sized businesses in mind, this guide is optimized to target keywords such as “free software risk assessment tool”, “cybersecurity risk scorecard”, and “AI-driven vendor risk analysis.”
Whether you’re using our tool to evaluate OpenOffice, LibreOffice, or Microsoft Office, this guide gives you the insights to make informed decisions.
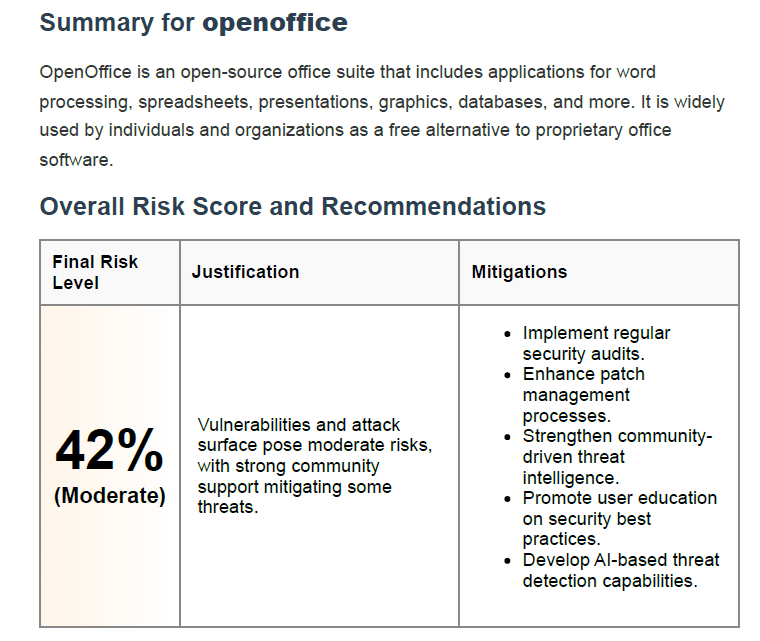
Executive Summary & Final Risk Score
What Is the Executive Summary? The executive summary provides a high-level overview of your selected software. It identifies the type of application (e.g., open-source office suite), its common usage, and the core reason for the risk analysis.
Understanding the Final Risk Score Your risk score (e.g., 42% – Moderate) is based on multiple weighted cybersecurity factors. This score provides a general snapshot of your current exposure to threats.
Why It Matters This score helps prioritize decisions: whether you should continue using the software, apply updates, or look for safer alternatives.
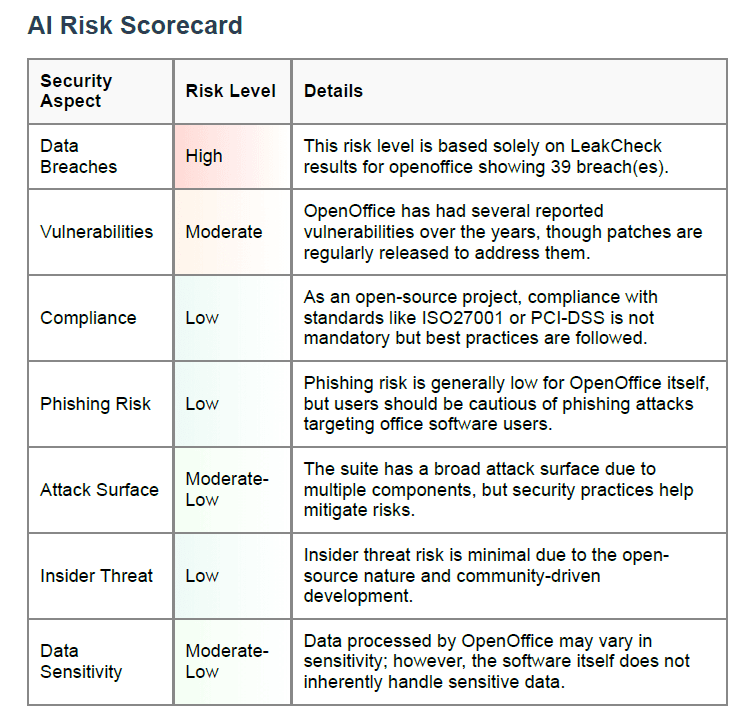
AI Risk Scorecard Explained
The AI Risk Scorecard breaks down risk across seven critical areas:
- Data Breaches Risk: High — Based on breach databases like LeakCheck, your software might have multiple past breaches. For OpenOffice, 39 breaches were detected【leakcheck source】.
- Vulnerabilities Risk: Moderate — Vulnerabilities exist but are often patched. Staying updated is crucial.
- Compliance Risk: Low to Moderate — Open-source tools usually follow best practices, but aren’t certified (like ISO 27001).
- Phishing Risk Risk: Low — Office software itself isn’t typically the target, but user training is advised.
- Attack Surface Risk: Moderate-Low — Multi-component software increases attack vectors, although mitigated by design.
- Insider Threat Risk: Low — With no internal employee structure, open-source risks from insiders are minimal.
- Data Sensitivity Risk: Moderate-Low — While sensitive data may be handled, the software does not directly manage classified info.
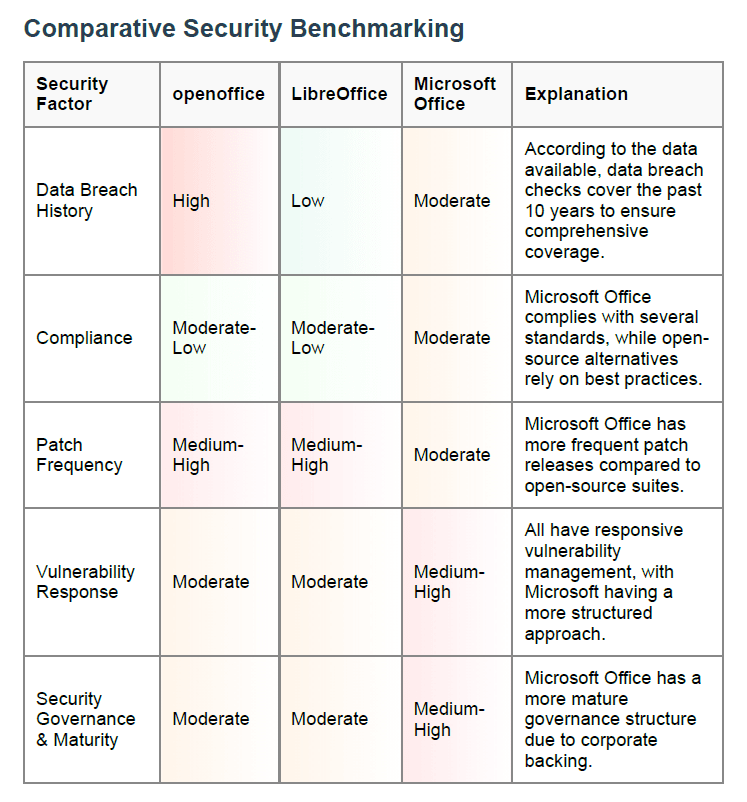
Comparative Security Benchmarking
Why This Matters This section compares your selected software against similar tools like LibreOffice and Microsoft Office. It helps determine how your current tool stacks up.
Key Takeaway Microsoft Office ranks highest in patching and governance, while LibreOffice fares better than OpenOffice in breach history.
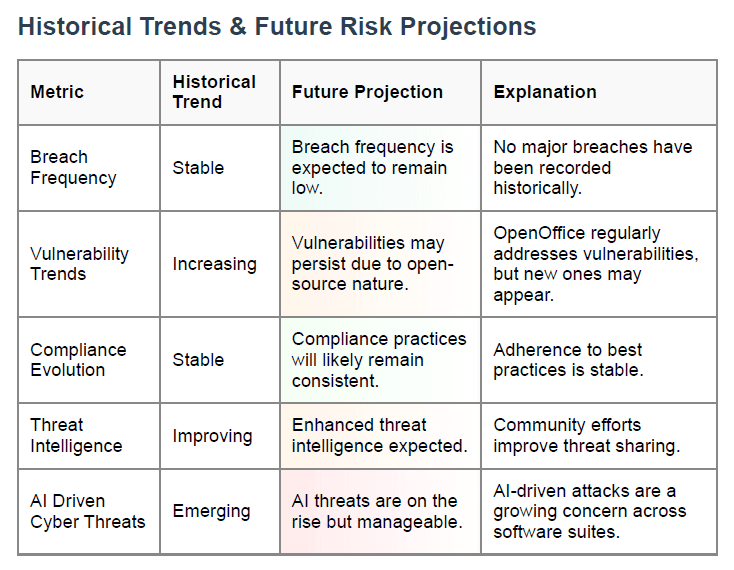
Historical Trends & Future Risk Projections
What This Section Shows This section forecasts your software’s security trajectory based on past trends.
Breakdown of Trends
- Breach Frequency: Stable
- Vulnerability Trends: Increasing
- Compliance Evolution: Stable
- Threat Intelligence: Improving
- AI-Driven Cyber Threats: Emerging
Why It Matters Forecasts help you prepare for upcoming threats, even before they become widespread.
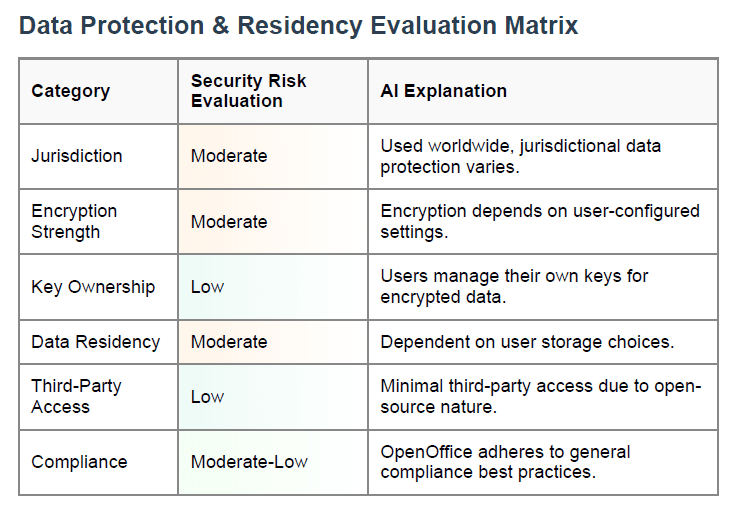
Data Protection & Residency Evaluation
Six Core Risk Dimensions This matrix evaluates where your data is stored, who manages encryption keys, and compliance posture.
Action Items If your software doesn’t offer built-in encryption or regional compliance, consider:
- Adding third-party encryption tools
- Hosting data in compliant jurisdictions
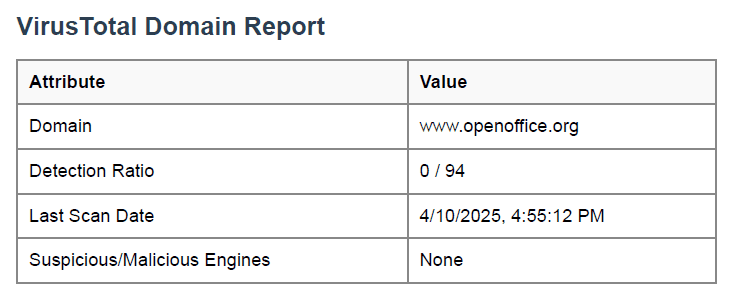
VirusTotal Domain Scan Summary
Understanding This Feature This component checks the domain (e.g., www.openoffice.org) for known malware or suspicious activity.
Example Report
- Detection Ratio: 0 / 94 (clean)
- Last Scan Date: April 10, 2025
- Engines Flagged as Suspicious: None
What This Means Your software’s website is safe to access. This doesn’t guarantee full application security, but it’s a good sign.
How to Use This Report Effectively
Step-by-Step Guide
- Review Risk Scorecard to identify weak spots.
- Compare Benchmarks to evaluate software alternatives.
- Examine Historical Trends to predict future threats.
- Use Data Protection Matrix to audit storage and encryption setup.
- Act on Recommendations (patching, monitoring, employee training).
Prioritize These Keywords When Searching for Solutions
- Free cybersecurity risk tool
- AI software risk scorecard
- Software vendor risk audit
- Open-source software vulnerability test
Conclusion: Empower Your Cybersecurity Strategy
Using a free software risk assessment tool like this gives your business the competitive edge it needs to stay ahead of digital threats. With AI-driven analysis, vendor comparison, and historical forecasting, your team can:
- Improve cyber hygiene
- Reduce vendor-related risks
- Make confident decisions about the software stack
If you haven’t tried it yet, generate your own free report at AcraSolution.com and unlock smarter risk mitigation today.